Our Co-Founder and CTO Brooklyn Zelenka recently gave a presentation on skip ratchets at the Strange Loop conference in St. Louis. Brooklyn created skip ratchets as a result of her work on Webnative File System in order to move more efficiently across data in a hash chain.
Let's Talk About Hash Chains!
Before we dive into skip ratchets, let's review hashes and hash chains. A hash uniquely identifies content and cannot be reverse-engineered. When we create a hash, data goes in but doesn't come back out. Furthermore, a certain amount of data is destroyed in the process as it's turned into a hash. All of this makes hashes very secure, which is why we use them in WNFS! A hash chain then, is a series of hashes linked together like Russian nesting dolls, where one hash is a hash of the hash before it, and so on.
Deterministic Skip Lists
A skip list allows a developer to skip large and small chunks of data as an alternative to going through each element one by one. This is like taking an armful of books off a book stack instead of one book at a time until you get to Alice's Adventures in Wonderland at the bottom. The goal is to get to the first layer as efficiently as possible.
The Skip Ratchet
The skip ratchet builds on the idea of deterministic skip lists by applying them to hash chains. The developer starts at X hash. They don't know where in the hash chain they are (they could be at number 1 or number 1,000,000). If their goal is to get to X + 10^62, they can skip ranges of hashes (called epochs) to get there using the skip ratchet.
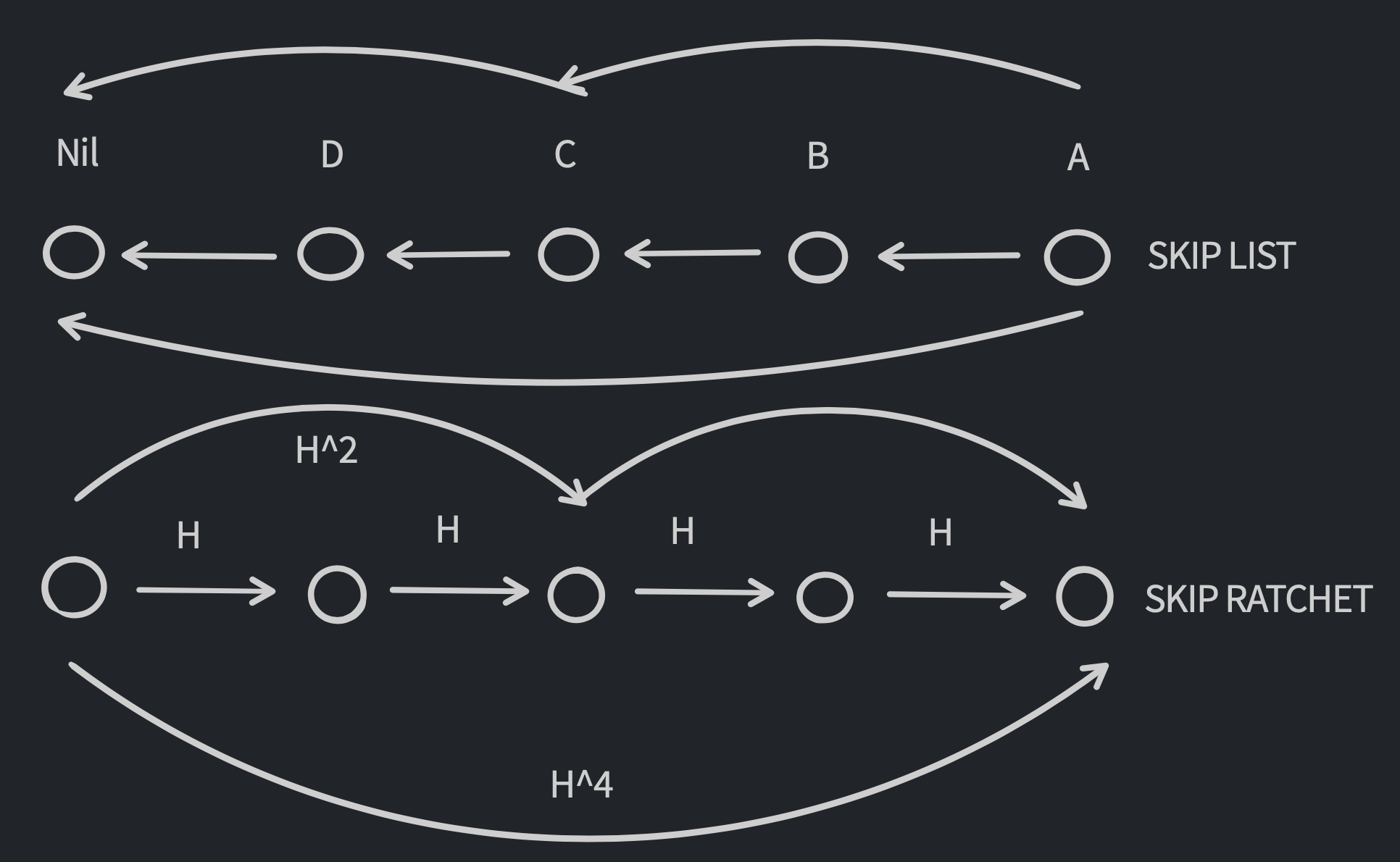
Benefits of Skip Ratchets
In WNFS we increased security by adding a randomly generated number to X. This obscures X's order in the chain even more. You can also limit read access by choosing to only share a range of hashes with another individual, thus giving the user more control over their own data.
Use Cases
We use skip ratchets in our Webnative File System as we mentioned, but there is a variety of other use cases popping up too. Temporal encryption, winternitz signature schemes, one-time passwords, and micropayments with electric coins can all utilize skip ratchets.
Learn more about skip ratchets by reading Brooklyn's paper and watching the Strange Loop presentation below.
