We were delighted to be joined by John from Source Network for our latest edition of Fission Tech Talks!
John spoke about the different components of Source Network, including DefraDB, a p2p database, how Source uses IPFS, and some ideas about interop with UCAN.
Decentralized Databases
Source Network empowers developers to deploy user-centric decentralized databases.
John realized that there were problems with the way data is handled today:
- Fragmentation - Data is unstructured and scattered across apps, devices, and file management system silos, making it time-consuming and laborious to manage.
- Imprisonment - Users are stuck behind walled gardens that don't allow data to move easily across services.
- Vulnerability - When all our data is stored in one place, it becomes an attractive target for bad actors.
John realized that a viable solution would require decentralized data that was:
- Interoperable - Break down the walled gardens and replace them with open data models.
- Controllable - User-owned data is key, as users should be able to move their data property around just like they do their physical property.
- Secured - Cryptographic protocols can help secure data, putting users at ease.
With these three characteristics in mind, John created DefraDB or Decentralized Infrastructure Database. What makes DefraDB unique?
DefraDB is:
- Deployable anywhere
- Uses no SQL
- Uses P2P protocols
- Uses cryptographic state proofs
- Employs CRDTs
Authorization
In the authorization world, there are two main paths - access control lists and object capabilities. In 2019, Google published Zanzibar, a paper explaining how they handle authorization across their many services. It uses access control lists but with relationship-based access control rather than role-based access control.
First, you write a tuple that includes subject, relation, and object. Then, you check if a permission exists and run an expand call that acts as a reverse lookup over a user set. It operates as a Consistent and Partition-Tolerant System.
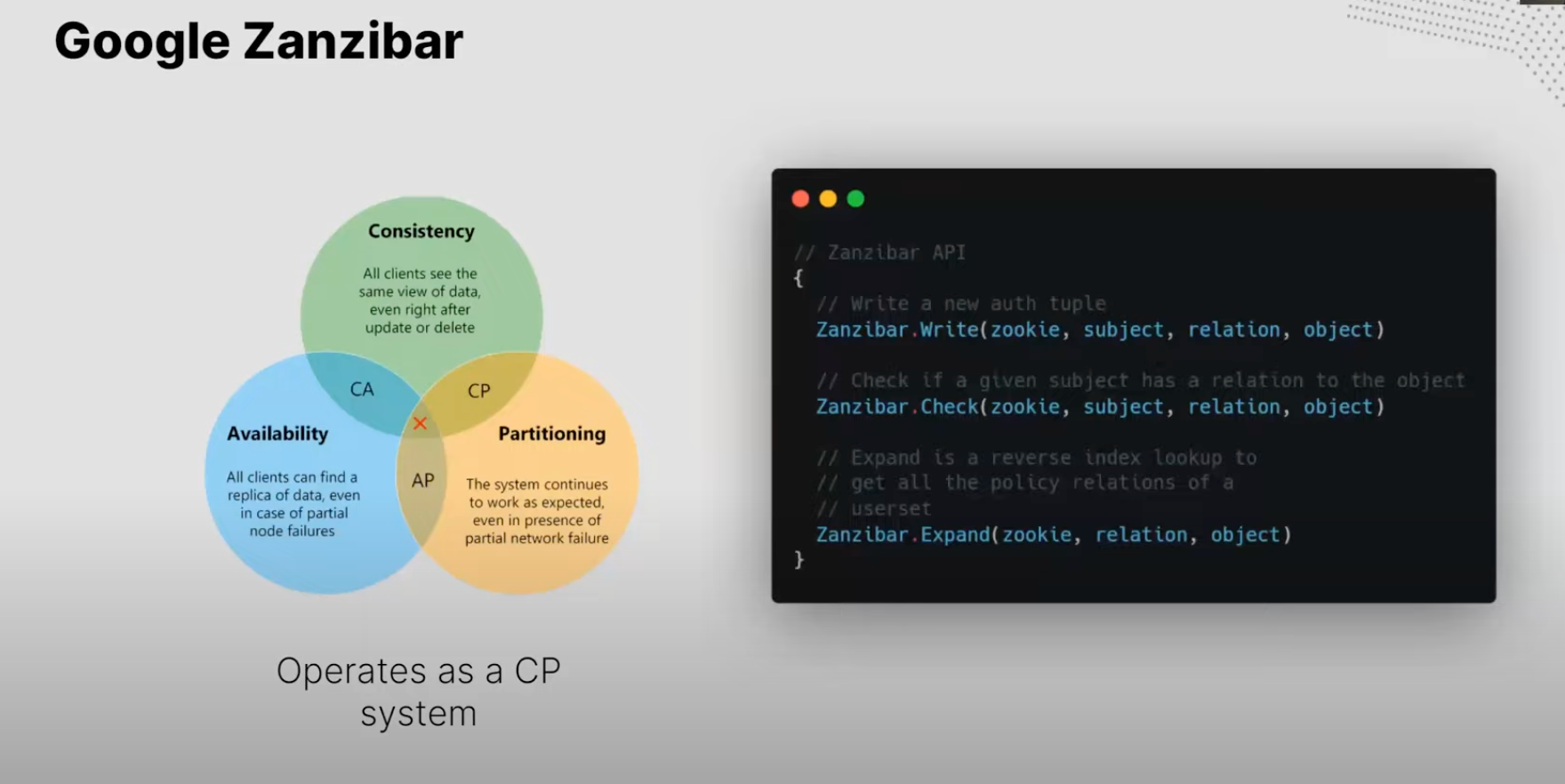
The Zanzibar API is centralized, so Source Network created a decentralized implementation of Zanzibar called Zanzi. The Source Hub trust protocol powers it.

Now, let's turn to the other type of authorization - object capabilities. With object capabilities, revocation can be challenging when you have to get refreshed tokens after the original ones expire. Therefore, Source Network created Zazu, which is Zanzibar Authorization with UCANs
The Zanzibar service mints the token rather than the individual, eliminating the interactivity problem. Then it goes back to the traditional UCAN spec the rest of the way down the chain.
If you'd like to learn more about Source Network's DefraDB, Zanzi, or Zazu, please visit Source Network, join the Discord, or explore the DefraDB repo.