A recap of the 2022 CascadiaJS Conference.
Fission recently returned from the 10th annual CascadiaJS Conference at the stunning Sunriver Resort in Oregon. Nestled in the Cascade Mountains of the Pacific Northwest, this premier conference brought together 650 developers in the region to learn, build relationships, and advocate for an Open Web.
Our Co-Founder and CTO Brooklyn Zelenka gave a presentation titled The Dark Forest: Private CRDTs as Global Database. In it she lays out three characteristics necessary for user-owned encrypted data on P2P social networks, local-first apps, and resilient client-side apps, and how to implement them using decentralized web tools and techniques.
Verifiable
Today the web is organized in a location-based system. A soft link directs you to a page you assume or hope contains the information you are searching for or is supposed to be there. Sometimes this is not the case because pages can get moved around, resulting in broken links, or a person can edit the information on the page and you no longer have access to the original data.
Brooke proposes utilizing content addressing to not only verify that the data you're requesting is the data that is pulled up on the screen, but it organizes the web in a more intuitive content-based system that is low or no-trust and self-verifying.
CIDs, or content identifiers, are hard links that point to a specific version of data that can never be deleted. They are a consistent way to reference data.
Imagine you enter your local library and you want to check out a book. Do you ask the librarian to find you the book located on the fifth stack, third shelf, and 27th position, or do you ask them to help you find My Inventions: The Autobiography of Nikola Tesla?
By searching for the content address rather than a location, you end up with exactly the data you wanted (instead of a book on Thomas Edison).
If you want to dive more into content addressing, ProtoSchool has a great tutorial.
User-Controlled Private + Portable Data
Data can be encrypted and stored in what's known as a cryptographic tree structure, or cryptree. Multiple cryptrees are a forest, and the forest is dark because it's encrypted. (Hence, the title of Brooke's presentation!) Cryptrees ensure that a user has complete control over who has access to their files by giving every file and every folder a unique key. Files can be accessed both on and offline. This is also key to working natively in the web browser with WASM and using tools like Fission's Webnative SDK, a local-first edge computing toolkit, to make web programming more streamlined.
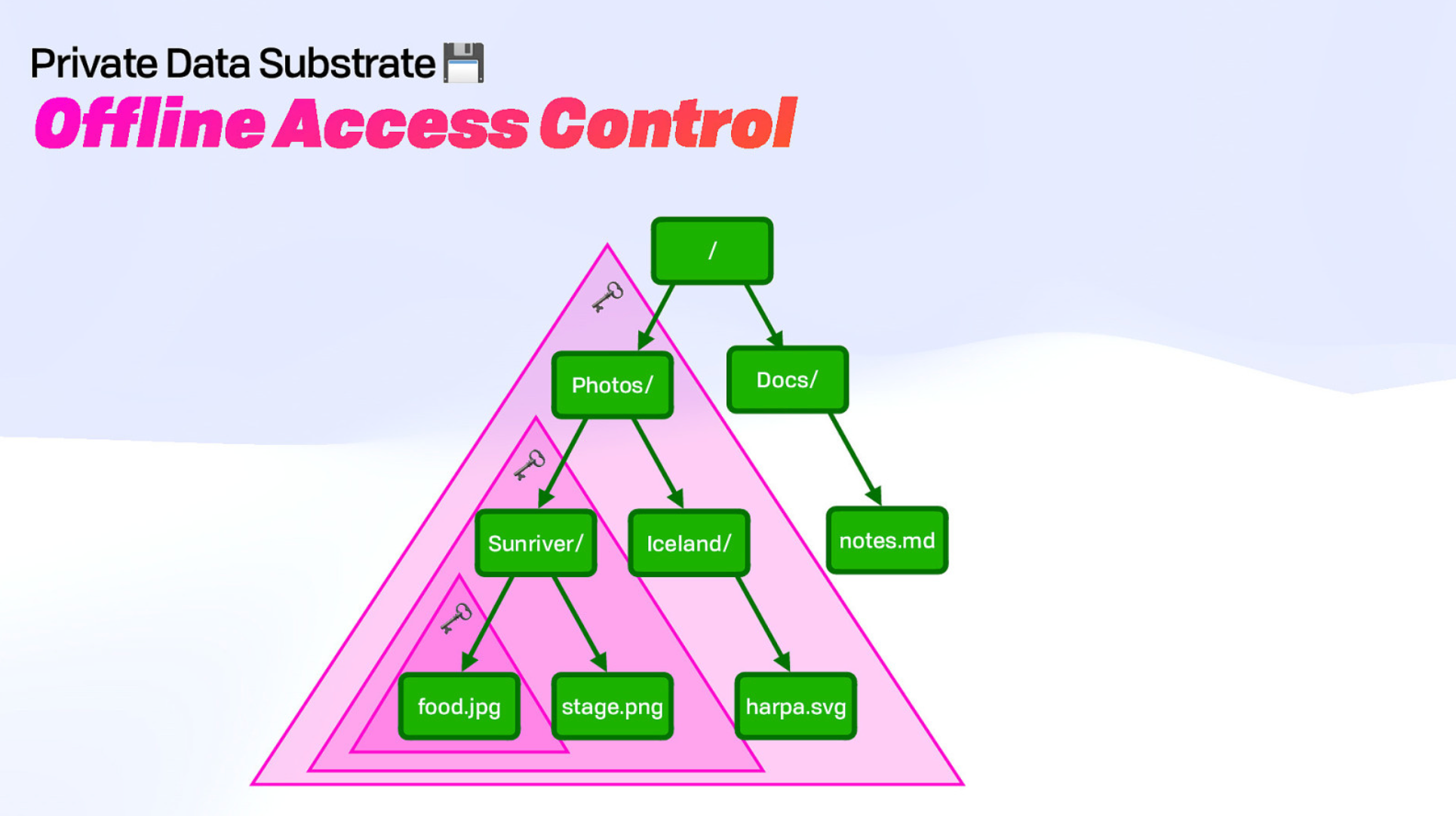
Now, you might think that this type of access/permissions structure already exists in the centralized apps you use today, but this data is not encrypted nor portable at the user level. Cryptrees ensure that not even the third-party app can delete or lose your content.
Collaborative + Concurrent
Finally, for people to work together collaboratively and efficiently, users must be able to work both synchronously and asynchronously, on and offline. Cloud-based docs and spreadsheets already exist that allow you to do this, but CRDTs, or Conflict-free Replicated Data Types, require less user interaction and can still be used in decentralized P2P networks using optimistic replication.

Thank you so much to Carter, Carrie, and the whole team & attendees of CascadiaJS for such an enjoyable event.
If you'd like to learn more about Brooklyn's work, you can follow her on Twitter at @expede. Her presentation slides can be found here, and we'll share the video of her presentation when it's available.
